1. Approach
The purpose of the Information Security department is to enhance Trust to any Service or Product by protecting the most valuable assets any type of organisation or business.
This purpose should be served by designing and implementing a structured, flexible, and trustworthy ecosystem that will use the collective power of People, Processes and Technology.
Netcompany-Intrasoft takes a holistic and proactive approach to security, emphasizing on proactive risk management, integration of resilient and cost-efficient controls, and investing on continuous improvement, to help its customers achieve their mission.
Our team of Information Security experts offers the joint view of multiple information and cybersecurity disciplines needed, to multiply the opportunities opened by trustworthy Services and Products, while successfully identifying and managing potential threats to supportive operations.
This team works closely with you to understand your unique needs and develop a customized solution that fits your objectives, based on international, yet flexible to customisation, best practices, and frameworks.
2. Why Choose Us?
Netcompany-Intrasoft is a multinational IT services company that provides a range of services, including security consultancy and solutions. The company has a reputation of delivering high-quality, reliable and efficient IT solutions to clients across various industries.
Our team of highly skilled and experienced security consultants can help organisations identify potential security risks, implement security controls, and improve their overall security posture. The security solutions offered by Netcompany-Intrasoft are designed to be flexible and customizable, to meet the specific needs of different organisations.
Netcompany-Intrasoft also has a proven track record of successfully delivering security projects of any scale on-time, and within budget. The company utilizes the latest technology and best practices in the field of security, to provide effective and innovative solutions that can help organisations achieve their security goals.
The combined expertise of Netcompany-Intrasoft further leverages its security consultancy and solutions for the emerging digitalization path of our societies. Ensuring Information Security, while deploying a wide range of Leading Edge Technologies, such as Artificial Intelligence, Machine Learning, Big Data Analytics, Operational Technology and Blockchain, as well as IT services such as Network Solutions, Cloud Computing and Software Development, we bring value, efficiency and trust to existing and future operating and service delivery environments.
Our unique combination of expertise, experience and wide range of collaborating services has made Netcompany-Intrasoft a trusted partner for any organisation looking for security services and solutions.
Netcompany-Intrasoft is a trusted partner
- Expertise in the field of security with extensive industry experience
- Strong reputation in highly demanding markets, such as EU organisations and Critical Infrastructures
- Proven track record of successful implementation of security solutions
- Wide range of services and offerings
- Integration capabilities with existing systems
- High-quality customer service and support
- Effective and efficient delivery of projects
- Ability to provide tailored solutions to meet specific needs
- Use of leading-edge technologies and international best practices
- Strong partnerships with leading security vendors
- Large and multifaceted team of experts dedicated to your success
- Commitment to stay ahead of the evolving threat landscape
3. What can Netcompany-Intrasoft do for the customers?
Information Security is an integral part of any organisation. Our team can help organisations and individuals be protected from cyber-attacks, as well as prevent data breaches, identity theft, and other types of cybercrime. In addition, we focus to help organisations evaluate the effectiveness and efficiencies of their cybersecurity and resiliency programs. It is essential for organisations to have strong cybersecurity measures to protect their data and customers. We offer both consultancy and technology services and solutions for all major enterprise and public sectors, as well as European Institutions. Our team has a holistic security approach, and all solutions are adapted to the customers’ needs.
Ways of engagement:
- Security Consultancy: Provide expert advice and guidance on security risks and best practices to help organisations improve their overall security posture
- Security Solutions: Design, implement and maintain custom security solutions to meet the specific needs of each customer
- Integration Services: Integrate security solutions with existing systems to improve efficiency and reduce complexity
- Secure Development & IT Operations Services: Provide a wide range of IT services including software development, data analytics, cloud computing, and more, to provide integrated and comprehensive IT solutions
- Tailored Security Solutions: Provide tailored security solutions that are specifically designed to meet the unique needs of each customer
We provide value by:
- Protecting sensitive data: We provide services and solutions to the organisations to prevent unauthorized access to sensitive information, such as customer data and financial records
- Maintaining business continuity: We provide guidelines and consultancy services to help organisations prevent disruptions caused by cyberattacks, allowing organisations to continue operating as usual
- Ensuring compliance: Many industries have regulations that require organisations to implement certain cybersecurity measures. We can help organisations comply with these regulations and avoid costly fines
- Enhancing reputation: We help organisations strengthen their cybersecurity awareness and cyber resilience and, as a result, build trust with customers and partners, improving their reputation and competitiveness in the market
- Staying ahead of evolving threats: Cybersecurity is an ongoing process, as new threats and vulnerabilities are constantly emerging. We help organisations be informed and stay up to date with the latest cybersecurity trends as a result, organisations can better protect themselves from emerging threats
- Strong Partnerships: We maintain strong partnerships with leading security vendors to provide customers with access to the latest security technology and solutions
4. Our services
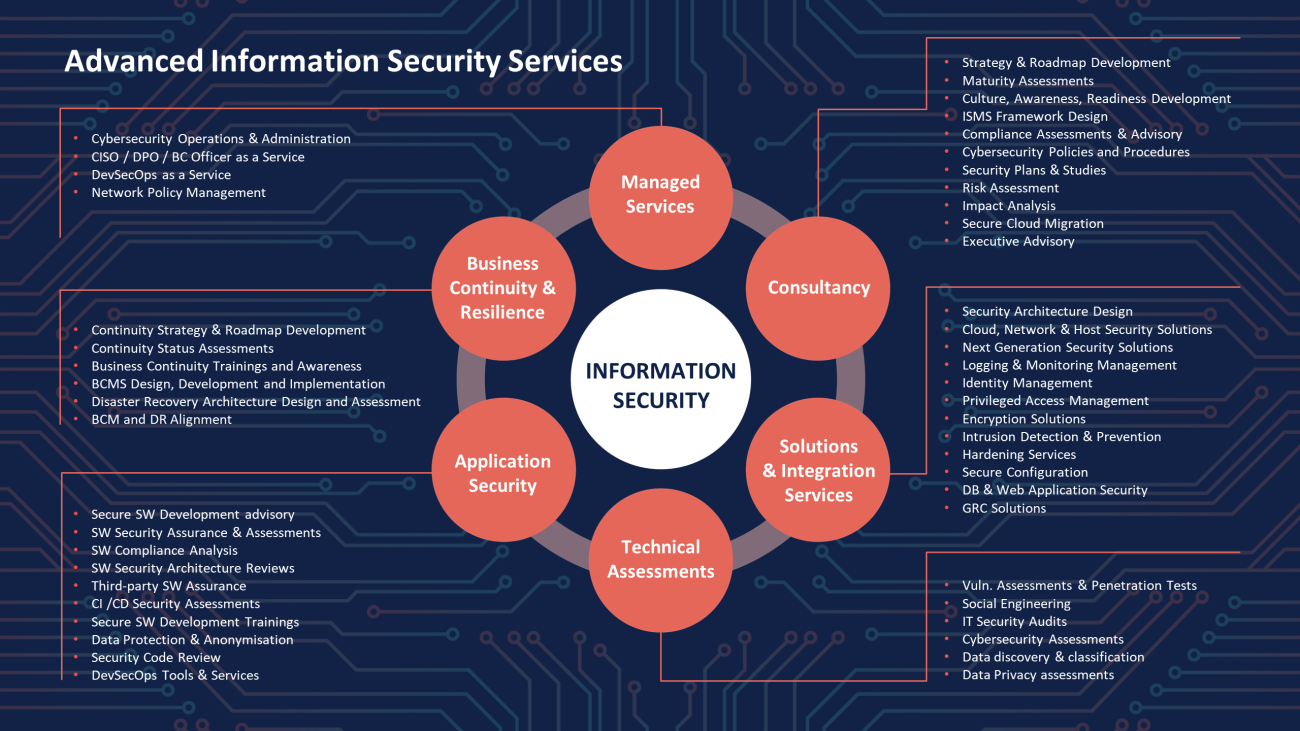
Managed Services is a comprehensive service that ensures that our clients’ cybersecurity posture is maintained and that the company is protected against any potential threats. By providing ongoing cybersecurity operations and administration, (CISO, DPO, BC officer, DevSecOps) as well as network policy management services, we can help identify and address any security issues that may arise, ensuring that the company's data and assets are protected at all times.
- Cybersecurity Operations & Administration: Our team of experts will handle all aspects of your cybersecurity operations and administration, ensuring that your systems are properly configured, monitored, and updated to keep them secure
- CISO / DPO / BC Officer as a Service: Our experienced professionals can serve as your Chief Information Security Officer (CISO), Data Protection Officer (DPO), or Business Continuity (BC) Officer, providing strategic guidance and support to help keep your business secure
- DevSecOps as a Service: Our DevSecOps experts can help integrate security into your development process, ensuring that security is built-in from the start and that vulnerabilities are discovered and remediated quickly
- Network Policy Management: Our team can help you develop and enforce policies to govern the use of your network and devices, ensuring that your organisation stays compliant and secure
Consultancy services provide expert guidance and support to organisations, in order to improve their overall security posture, reduce risks, and comply with relevant laws and regulations. The services include strategy development, maturity assessments, awareness and culture development, ISMS framework design, compliance assessments, policy and procedure development, risk assessment, impact analysis, secure cloud migration, and executive advisory. The importance of consultancy is to help organisations better understand and manage their cybersecurity risks, develop effective cybersecurity strategies, and stay ahead of evolving threats in today's digital landscape. Our consulting services can help your organisation establish a strong and resilient cybersecurity posture, protecting your critical assets and reducing the risk of cyber-attacks and data breaches.
- Strategy & Roadmap Development: Our experts can help you develop a comprehensive cybersecurity strategy and roadmap to ensure that your organisation is prepared for potential threats and that your resources are allocated effectively
- Maturity Assessments: Our team will assess your organisation's current state of cybersecurity maturity and provide recommendations for improvement. Our team is dedicated to helping you stay ahead of the evolving cybersecurity landscape, and we are committed to delivering actionable recommendations that can help you better protect your sensitive information and assets
- Information Security Awareness Training and Culture Development: Our team of cybersecurity professionals can assist you in developing a comprehensive information security awareness training and culture development program for your organisation. We understand that cybersecurity threats are constantly evolving, and your employees play a critical role in protecting your organisation's sensitive data and systems. Our services involve a customized approach tailored to your organisation's specific needs and goals covering a wide range of topics
- ISMS Framework Design: We can help you design a comprehensive ISMS framework through a systematic approach that includes policies, procedures, controls, and metrics that ensure your organisation is well-prepared for any cybersecurity threat. Our team has extensive experience in designing ISMS frameworks for a range of industries and organisations of all sizes
- Compliance Assessments & Advisory: Our experts can help you assess your compliance with relevant regulations and standards and provide guidance on how to meet and maintain compliance. Our team has extensive knowledge and experience in regulatory and industry-specific compliance and standards, including NIS2, GDPR, EU 2018/1725, PCI-DSS, ITSRM2, ISO/IEC 27001 and other industry-specific regulations. We stay up to date with the latest changes and updates to these regulations, to ensure that our clients are always compliant
- Information Security Policies and Procedures: Our team can help you develop and implement comprehensive policies and procedures to govern your organisation's cybersecurity practices. With our policy and procedure development services, you can establish a strong foundation for your information security program and reduce the risk of cyber-attacks and data breaches. We can help you ensure that your organisation is prepared for any cybersecurity threat and can respond quickly and effectively to mitigate any potential risks
- Security Plans & Studies: Our team can help you develop comprehensive security plans and studies, that ensure your organisation is prepared for potential threats and your resources are allocated effectively. We work closely with you to ensure that your resources are effectively allocated to address the most critical security risks, providing you with the confidence and peace of mind to focus on your core business operations
- Risk Assessment: Our team can assist you in identifying and assessing potential risks to your organisation's information security. We understand that identifying and mitigating risks is crucial to maintaining the confidentiality, integrity, and availability of your sensitive data. We can help you identify and mitigate potential risks before they turn into major incidents, ensuring that your sensitive data and information systems are secure
- Impact Analysis: Our experts can assist you in assessing the potential impact of a security breach or other disruption on your organisation. We understand that such incidents can have far-reaching consequences, including financial losses, reputational damage, and legal repercussions. By leveraging our impact analysis services, you can have greater confidence in your ability to respond to and recover from a security breach or disruption. We can help you mitigate the potential consequences of such incidents and ensure that your organisation can continue to operate with minimal disruption
- Secure Cloud Migration: Our experts can work with you to assess your organisation's readiness for cloud migration, identify potential risks and challenges, and develop a comprehensive migration plan that is tailored to your unique needs and requirements. We provide guidance on best practices for secure cloud migration, such as data encryption, multi-factor authentication, and network security protocols. Our team also assists with testing and validation to ensure that your systems are working as intended and that your data is protected
- Executive Advisory: Our experienced professionals can serve as a trusted advisor to your executive team, providing strategic guidance and support to help keep your business secure
Solutions & Integration Services aim to provide comprehensive security solutions and consultancy services, to help businesses and organisations protect their digital assets from potential threats and attacks. We offer a range of security solutions, including security architecture design, cloud, network and host security, identity management, encryption solutions, intrusion detection and prevention, and more. Our services are designed to help clients safeguard their digital assets, enhance their security posture, and achieve compliance with industry regulations.
- Security Architecture Design: Our team of experts uses the latest tools and techniques to design the most effective security architecture for your organisation
- Cloud, Network & Host Security Solutions: Our solutions ensure the security of your cloud, network and host systems, protecting against cyber threats and data breaches
- Next Generation Security Solutions: We stay ahead of the curve by providing the latest and most innovative security solutions, that keep up with the constantly evolving threat landscape
- Logging & Monitoring Management: Our logging and monitoring services provide real-time visibility into your security posture, enabling you to quickly identify and respond to potential threats
- Identity Management: Our identity management solutions secure and simplify the management of user identities, ensuring that only authorized users have access to sensitive information
- Privileged Access Management: Our privileged access management solutions help you secure and control access to your most critical systems and data
- Encryption Solutions: Our encryption solutions protect your sensitive data at rest and in transit, ensuring that they are unreadable to unauthorized users
- Intrusion Detection & Prevention: Our intrusion detection and prevention solutions provide real-time threat detection, enabling you to quickly respond to potential security incidents
- Hardening Services: Our hardening services enhance the security of your systems by applying industry-standard security measures and configurations
- Secure Configuration: Our secure configuration services help you ensure that your systems are configured in a secure and compliant manner
- DB & Web Application Security: Our database and web application security services protect your critical applications and data from cyber threats
- GRC Solutions: Our governance, risk, and compliance (GRC) solutions help you ensure that your organisation complies with relevant regulations and standards
- DDOS Mitigation: It is essential to recognize that DDoS attacks pose a significant threat to businesses. These attacks aim to disrupt the availability of your application or network, and the methods used to launch them may vary. Therefore, we offer DDOS Mitigation services to safeguard your network and prevent such attacks
- DNS Attacks Mitigation: We understand the severe impact of DNS attacks, including DNS hijacking and DNS DDoS attacks. These attacks can cause significant damage by swiftly rendering a website inaccessible, leading to user frustration, loss of revenue, and tarnished brand reputation. Hence, we offer DNS ATTACKS Mitigation services to protect your web presence and prevent such attacks from occurring
Empowering your Web Application Firewall capabilities: we understand the severe impact a business can have due to various potential threats to their applications, including:
- Application-Layer Attacks: Application-layer attacks can evade signature and reputation-based security solutions
- Web App and API Attacks: New application attack surfaces and increased threat thresholds are popping up due to the rapid adoption of APIs (ex. GraphQL APIs, OWASP Top 10)
- Security Automation for DevOps: Bring apps to market faster with lower cost and higher security efficacy
- Targeted Attack Campaigns: Active attack campaigns are difficult to detect from singular attacks
- Automated Attacks and Bots: Automated attacks and bots can overwhelm application resources
- Credential Theft: Attacks that steal application credentials or take advantage of compromised accounts
Hence, we offer Web Application Firewall services to protect your web presence and prevent such attacks from occurring.
We ensure Access Management: We provide tailored solutions, including zero trust app access, secure remote access, hybrid app access and robust endpoint security.
- Zero trust app access: Deploy zero-trust model validation based on granular context, securing every app access request
- Secure remote access: Gain end-to-end data encryption with highly customized authentication and access control to individual apps, networks, and resources
- Hybrid app access: Integrating with IdaaS providers like Azure AD, you can centralize authentication to all your apps—cloud-native, SaaS apps and those on-prem
- Robust endpoint security: Perform device security and integrity checks and deliver per-app VPN access without user intervention
Technical Assessments services aim to identify potential vulnerabilities and security risks in the clients' IT systems and applications. We offer a range of services, including vulnerability assessments, penetration testing, social engineering, IT security audits, cybersecurity assessments, data discovery and classification, and data privacy assessments. Our assessments are designed to provide clients with a comprehensive understanding of their IT security risks and vulnerabilities, and to help them enhance their security posture and compliance with industry regulations.
- Vulnerability Assessments & Penetration Tests: Our vulnerability assessments and penetration tests provide you with an in-depth understanding of your security posture, including any weaknesses and vulnerabilities that need to be addressed
- Social Engineering: Our social engineering assessments test the human element of your security, identifying areas where your employees are most vulnerable to attack
- IT Security Audits: Our IT security audits provide you with an independent and objective assessment of your security posture, enabling you to prioritize your security initiatives
- Cybersecurity Assessments: Our cybersecurity assessments help you identify the risks and vulnerabilities specific to your organisation, enabling you to take the necessary steps to mitigate them
- Data discovery & classification: Our data discovery and classification services help you identify and classify sensitive information, enabling you to implement the appropriate security measures to protect it
- Data Privacy assessments: Our data privacy assessments help you understand your organisation's obligations under relevant privacy laws and regulations, enabling you to ensure that you comply
Our application security services aim to help clients protect their software (web, mobile, IoT) and create secure products that sustainably enable digital transformation. We offer a range of consulting and technical services that can kick-start or further accelerate and mature application security programmes. With our application security services, you can feel confident that your organization's applications are secure and protected against potential threats.
Our application security experts take a hands-on approach with clients to help them integrate and automate security activities into the software development life cycle (SDLC). The goal is to embed best practices and a culture that shifts security left. Shifting left means that clients design software with security best practices in mind and are able to detect and fix potential security issues proactively.
Below you may find the Application security services offered by Netcompany-Intrasoft:
Consulting services
- AppSec and Secure Software Development Maturity Assessments: We specialize in conducting comprehensive application security maturity assessments that help organizations and address security gaps and weaknesses in their application development processes. Our team of experienced security professionals will work closely with you to evaluate your organization's application security practices and provide a detailed report of your current security maturity posture. Typical maturity assessment engagements are conducted using OWASP’s Software Maturity Assessment Model (SAMM), that has gained wide adoption in recent years and is on the path of providing open-source and anonymous benchmark data
- Application Security Strategy and Program Development & Execution: Building on the maturity assessment service, we can help your organisation in developing and implementing a comprehensive application security strategy that meets your unique business needs. Especially for the implementation part, we’ll assist you in developing policies and procedures, selecting, and deploying appropriate security tools, and training your staff on security best practices
- Application Security Threat and Risk Assessments: For specific software applications in your organisation, we can assist in the execution of risk assessments, so that potential security threats and vulnerabilities are identified. The identified risks can further feed into the definition of requirements and security controls that shall be designed and implemented
- Application Security Regulatory Compliance Assessments: The service is designed to help organizations identify and address security vulnerabilities in their applications, and to ensure that their applications comply with applicable regulations. Our team of experienced security professionals uses a proven methodology to assess the security of applications, including code reviews, penetration testing, and vulnerability assessments. Our assessments cover a range of regulatory requirements, including HIPAA, PCI DSS, and GDPR, among others
- Application Security and Secure Coding Training Services: Our training services are designed to educate developers, architects, and security professionals on secure coding practices, application security fundamentals, and the latest threats and attack vectors. Our training courses cover a range of topics, including secure coding principles, threat modelling, security defect management and more. Our training services can be customized to meet the specific needs of your organization, including the size of the audience, the skill level of the participants, and the type of applications you develop. We can deliver our training services onsite or online, depending on your preferences
Technical Services
- Application Security Architecture and Design Assessments: Our service will help you identify potential security vulnerabilities in your application’s design and provide recommendations for remediation. Our team of experienced security professionals will conduct a thorough review of your application's architecture and design to validate that secure design principles have been followed, and commensurate security controls are in place
- Application Security Verification Assessments: Our security verification assessment service focuses on independently attesting that a software application meets certain trust levels as these have been defined by the organisation. Typically, our experts conduct verification assessments against OWASP’s Application Security Verification Standards (e.g. ASVS, MASVS etc.), and check conformance against requirements specified therein per assurance level. Verification is achieved by executing code reviews, penetration testing, vulnerability assessments, configuration and documentation reviews
- DevSecOps Design and Implementation Services: Whether you're looking to integrate security into your existing development workflows, or you're starting with a brand-new project from scratch, we have the expertise and experience to help you build a secure, efficient, and effective DevSecOps pipeline. Our services include everything from initial assessments and planning to ongoing monitoring and support. Our experts maintain deep knowledge of all main and best of breed open-source tools related, but not limited, to: Software Composition Analysis (SCA), Static Application Security Testing (SAST), Dynamic Application Security Testing (DAST), Secret Scanning, Container Image Scanning, Infrastructure as Code scanning
- CI/CD Technical Security Assessments: Our service is designed to help your organisation to thoroughly evaluate the security of your CI/CD application stack and infrastructure. There is a variety of technologies and platforms that are commonly used for developing modern software and it has become essential to securely configure, deploy, maintain, and operate those to ensure consistent supply chain security. Our assessment delves in distinct phases of the software supply chain and aims to guide clients in levelling up the secure configuration and secure deployment defences for achieving source code integrity, build integrity and deployment integrity
- Application Security Source Code Reviews: Our team of experienced security experts uses industry-standard tools and techniques to analyse your code and identify any potential security issues. We'll provide you with a detailed report outlining any vulnerabilities we find, along with recommendations for how to address them.
We use widely accepted Secure SW Development Frameworks

5. Technical solutions and partnerships
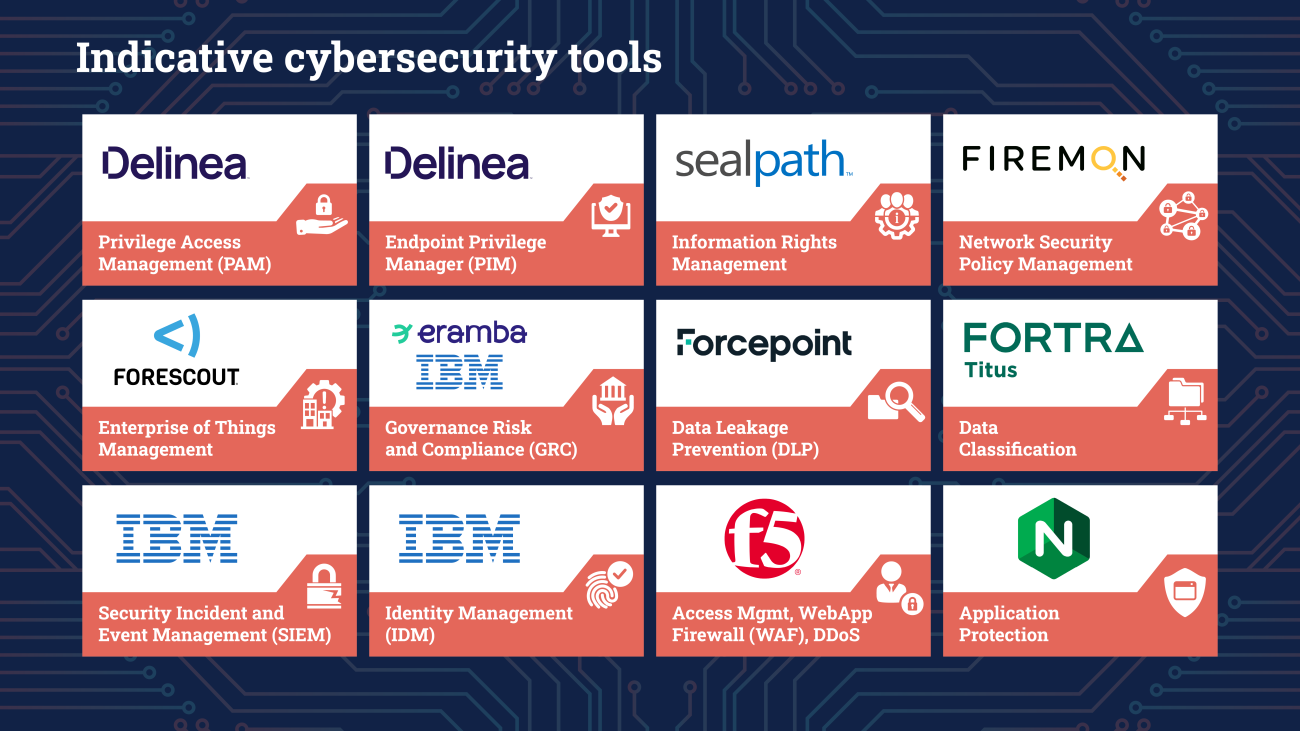
Netcompany-Intrasoft has a vast experience on multiple technical solutions and alternative vendors, ranging from large-scale solutions to open-source solutions. This approach has made us a vendor free service provider, being able to design and implement in best-of-breed or cost-efficient approaches. Typical solutions include:
- Network security solutions
- Cloud security solutions
- Security Information and Event Management (SIEM) solutions
- Data loss prevention (DLP) solutions
- Business Continuity and Disaster Recovery (BCDR) solutions
- Vulnerability management solutions
- Security Configuration Management (SCM) solutions
- Identity and Access management (IAM) solutions
- Security assessment and compliance solutions
- Application security solutions
- Privilege Access Management (PAM) solutions
- End Points Admin Rights Management solutions
- Information Rights Management solutions
- Enterprise of Things Management solutions
6. Our team
Netcompany-Intrasoft team blends highly experienced professionals, including former security officers, senior security consultants and deep-dive security engineers from EU Projects, companies from various industries, including financial, telecommunications, energy and public sectors. We are proud of our team of highly qualified and certified cybersecurity experts who are dedicated to delivering exceptional services to our customers. Our team holds a wide range of certifications, including CISM, CISA, CGEIT, CDPSE, CRISC, ISO 27001, ISO 22301, ECSA, CEH, CND, CASE, Security +, CASP +, Network +, CISSP, GCED, CCSP, OSCP, ITIL, PRINCE2, COBIT, EUSA, etc. These certifications demonstrate our team's extensive knowledge and expertise in cybersecurity and IT service management, and our commitment to staying up to date with the latest industry trends and best practices.
Our team's certifications are a testament to our commitment to excellence and our ability to deliver exceptional results for our clients. We believe that our team's extensive experience and knowledge, coupled with their dedication to staying up to date with the latest industry standards, makes us the ideal partner for all your cybersecurity and IT service management needs.

7. Testimonials, events and announcements
Testimonials:
Netcompany-Intrasoft has been a valuable partner for every company in its journey to improve its security posture. Our team of experts conducted a thorough risk assessment and designed a comprehensive security solution that met business’s specific needs. The implementation is smooth, and the solution is highly effective in preventing security incidents. The continuous monitoring and response plan are provided to customers with peace of mind. All companies are very satisfied with the quality of service and the results achieved and would highly recommend Netcompany-Intrasoft to anyone looking for a reliable and trusted security partner.
Netcompany-Intrasoft has recently won several landmark contracts that demonstrate our leadership and expertise in the cybersecurity and IT industries.
- One of these landmark contracts is the EU Digital Wallet contract, which we won in recognition of our innovative solutions and commitment to security. This project will enable us to work closely with the European Union to develop a secure and user-friendly digital wallet platform for citizens across Europe
- In addition to the EU Digital Wallet contract, we are also proud to have won the ECB innovation contract, which will allow us to work with the European Central Bank to develop new and innovative solutions for the financial industry. The services provided by the Netcompany-Intrasoft consortium will primarily target the development of innovative prototypes, Proofs of Concept and Minimum Viable Products especially related with the Banking Supervision and Central Banking operation domains. For accelerating the relevant use cases, the consortium will provide at the ECB services raising the awareness of emerging technology trends and key ecosystem players
- We are also pleased to announce that we have been selected to support the European Patent Office’s business analysis efforts, where we bring our expertise in cybersecurity and IT solutions to help streamline their operations and enhance their security posture. Netcompany-Intrasoft provides their expertise for the identification, articulation, and analysis of business needs of the EPO. Furthermore, the consortium defines solutions and also improvements to business processes in line with identified business goals and objectives
8. Indicative Projects and Customers
Netcompany-Intrasoft has developed and supported the European Commission's Authentication System (ECAS), which provides secure access to EU web applications and services.
Netcompany-Intrasoft has provided Software application and cybersecurity services to the European Union Intellectual Property Office's (EUIPO).
Netcompany-Intrasoft has delivered IT security services to the European Parliament, including vulnerability assessments, penetration testing, and security incident management.
Netcompany-Intrasoft has also provided cybersecurity consulting services to major clients such as the National Bank of Greece, Alpha Bank, and Eurobank in Greece.
Netcompany-Intrasoft worked with the European Commission's Directorate-General for Informatics on the development of a secure data exchange platform for EU institutions, called CIRCABC (Communication and Information Resource Centre for Administrations, Businesses and Citizens).
Netcompany-Intrasoft provided IT security and consultancy services for the European Central Bank (ECB) as part of a long-term contract to support the bank's IT operations.
Netcompany-Intrasoft worked with the European Patent Office (EPO) to provide business analysis and project management services for the implementation of a new electronic patent application processing system.
Netcompany-Intrasoft has provided IT security services to the European Aviation Safety Agency (EASA) including WAF, Access Management, SSO and SSL VPN. Netcompany-Intrasoft has also provided cybersecurity and infosec services to various national government agencies and private sector clients.

